Electronic Network Communication
J. K. Buda
Introduction
The advent of the electronic age has brought about many remarkable changes in patterns of personal and public communication. Electronic media such as telephone, radio, and television have indeed altered the nature of communication itself.
In facilitating communication, media have always imposed characteristic physical constraints upon the nature and content of the information being transmitted.
The present study seeks to identify some of the characteristics and effects of one of the most recent electronic media: that of message exchange by computer network.
Most of the observations upon which it is based were made during the course of a twelve-month study leave made possible by the generous support of both Otsuma Women's University and the Japan Association of Private Colleges and Universities, and are the result of over five months of active participation in nine electronic networks in both Canada and the United States.[1]
Communicating by Computer
In its simplest form, electronic communication consists of an exchange of messages and information between two computers.
Once a message has been composed upon a computer screen it can be stored on a magnetic or optical medium, or it can be sent to an output device such as a printer. It can also be sent to another computer. The two computers need not be in physical proximity, nor need they be physically connected by cable. It is just as simple to link the computers by telephone, requiring only that a small electronic device called a modem (a compound of MOdulate-DEModulate) be installed between the computer and the telephone outlet.
An exchange of messages between two computer users A & B might take the following form: A composes a message upon his computer. When he is satisfied with the result, he dials B's telephone number. As soon as the telephone connection is made, A's computer sends the message to a modem, which converts the incoming digital information into analog signals and feeds them into the telephone line. At B's end of the connection, another modem reconverts the analog signals into digital information, and B's computer shows the incoming message upon its screen. B is then free to read the message, or save it onto a magnetic disk or other storage medium for future reference. He may then choose to write a reply to the message and send it to A via the reverse of the route described.
Although such an exchange of messages (or any form of data) is extremely simple and efficient, it does have certain inherent limitations, not the least of which is that it needs to take place in real time. In other words, both computers need to be switched on and in a mode enabling the transmission or reception of messages. It does not lend itself to the exchange of messages among a large number of computer users pursuing different patterns of work and leisure, and living in widely differing time zones.
The Bulletin Board
If someone wishes to convey an urgent message to a large number of people, the telephone is not the best or most efficient way. If, for example, the registrar's office of a university needs to inform a thousand or more students that there will be no classes next week, calling each and every student's home and transmitting the message verbally would take far too long, and would not necessarily result in the message reaching everyone for whom it is intended. Some students might not be at home when the call is made; some students might indeed be on campus at that very time; yet other students might not have access to a telephone at all.
In such a situation the most simple and efficient form of communication is the bulletin board. Students are made aware of the existence of the board and instructed to refer to it whenever they visit the campus. A message posted on such a board will be seen by almost every student within a day or two of its posting, and each student will read it at his or her convenience.
The electronic equivalent of the bulletin board is likewise an efficient way of broadcasting messages among a large number of people who are not in real-time contact with one another.
Single-node Networks
In essence, an electronic bulletin board consists of a host computer used to store messages for retrieval by a large number of users accessing the system at a time of their own choosing. For the purposes of this discussion we shall refer to such an electronic bulletin board as a single-node network, all the messages being transmitted or received through a single node. Such a system is often referred to as a BBS (Bulletin Board System). Some major single-node networks provide other facilities in addition to one or more bulletin boards — notably data and information — and are generally referred to as information systems. The principle, however, is the same.
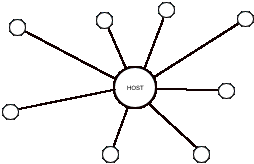
Fig. 1
A small BBS may consist of a single personal computer running for only a few hours each day, accessed by anything from a few dozen to a few hundred users. The host computer may be located in someone's home or office, and the service provided on a voluntary non-profit basis. If the number of users is small, and the message traffic light, the BBS will have only one message area where all the messages, irrespective of content, are posted and read. If the number of users is large, the BBS will probably be divided into several message areas, each one catering to a different interest group. Each message area might in turn be subdivided into a number of discussion topics, with new topics being opened and old topics closed as necessary.
At the other extreme, a commercial information system might consist of multiple main-frame computers processing messages from several hundred thousand users, twenty-four hours a day. Such an information system might also provide a number of local access points to enable users to enter the system by dialling a local number, thus economizing on telephone charges. These local access points are often referred to as 'nodes', but the system as a whole may still be considered single-node, for all the messages are received, processed, stored, and transmitted by a single computer nexus.
It should also be noted that, in addition to bulletin boards, information systems also provided many other commercial services such as online catalogue shopping, access to financial and technical databases, direct use of flight information and booking systems, and even online personal banking.
Both BBSs and information systems also support the exchange of computer software between users, files being uploaded and downloaded to the host computer in the same way that messages are posted and read.
Multi-node Networks
It is also possible to link several geographically separate host computers in an amorphous, decentralized network. Many such networks have evolved over the years, linking universities, major computer installations, and various interest groups. In a system such as this the entire network can be viewed as one enormous bulletin board. Although the principal activity of posting and reading messages remains unchanged, the physical flow of information in such a multi-node system is much more complex.
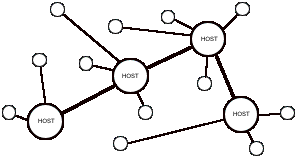
Fig. 2
In many ways the flow of messages within a multi-node system can be likened to the flow of letters within a postal service. In the latter, letters dropped in the nearest postbox are routed from post office to post office until they reach the one nearest to the addressee. From there the letter is delivered by hand. In a multi-node system, messages are posted to the nearest host computer, from where they are passed along to other computers, eventually reaching the host computer nearest to the user for whom the message is intended. The message will then be stored in that computer until the next time that user accesses the system and reads the backlog of waiting messages.
The above example compares the flow of private messages within multi-node electronic networks to the flow of letters within a postal system, but it should be remembered that in multi-node networks public messages comprise the bulk of message traffic. In contrast to the postal service model, where a single message follows a single route to single destination, a public message in a multi-node network will be routed to a number of destinations and made available to thousands of users. The effect of this characteristic upon the nature of the messages being transmitted will be discussed later.
Although both single-node and multi-node networks provide facilities for private messages (or E-mail) which can only be read by the addressee, we shall limit subsequent discussion to the public message traffic in both systems.
Having outlined the major functions of single-node networks such as BBSs or information systems, and multi-node networks such as those linking universities or user groups, it may help to illustrate these functions by offering two fictional examples of representative online sessions.
Single-node Online: Tom Smith returns home one evening and after supper decides to check recent messages on the Alpha BBS to which he belongs. He became a member by contacting the system operator of the BBS and registering his name and address. In return he was given an electronic address in the form of a nickname, a secret password to identify him, and also the right to access the BBS for up to 45 minutes each day.
Whenever he accesses (or 'logs on') to the BBS he is asked for his address and password, and if these match those registered in the computer, he is allowed to make free use of the system for the time allowed.
Since his last access three days ago, a total of sixty new messages have been posted on the BBS, ranging from ongoing discussions to requests for information. After reading the backlog of messages, he feels he would like to post some messages of his own, perhaps a comment he would like to add to a discussion, or a response to a query.
By sending various commands from his computer keyboard at home, Tom activates the BBS's text editing facility and composes his messages online, inputting them directly into the system. While he is typing at home, the Alpha BBS acts as a remotely-controlled word processor, enabling him to correct or delete mistakes, or find and replace words or phrases.
When he has finished writing his messages, the BBS stores them in its memory bank, waiting be displayed to the next user accessing the system. Tom's messages will be identified by headers containing such information as the name or address of the sender, the time of posting, and the general topic to which they belong.
Multi-node Offline: Sally Green's university is connected to the Omega computer network, and she regularly reads the messages posted on the Environmental Issues forum of this network. Each day several hundred messages originating from universities throughout the world are posted on this forum, and reading them all would take more time than she has available.
Returning to her office after a lecture, she switches on her computer and accesses the Omega network via her university computer centre. Her university maintains an account with the network, and also acts as one of the host computers for the area in which she lives. She has compiled a computer program which automatically reads only those topics of the Environmental Issues forum she is interested in, and stores them in a special file in her computer. This automated reading of messages saves online time and allows her to read the messages at leisure after she has 'logged off' the network.
One of the messages calls for a reply. She composes this reply upon her own computer, using its word-processing function to create a considered and well-crafted message. When she is satisfied with the result, she logs on to the Omega network once again and uploads her reply as a single document file, thereby saving even more online time.
From her computer the message goes to the university host computer, and from there it is routed through the network, from computer to computer, until it eventually reaches the computer of the forum moderator, who may wish to check messages for suitability before allowing them to reenter the system as a batch (or 'packet'). The batch of messages will then flow through the network again, and will be routed to whichever host computers have asked to receive the Environmental Issues forum.
Sally's message appears on the network exactly as she wrote it, but with an extensive header and footer at beginning and end. The header contains information such as Sally's network address, the time of posting, the route of posting, and whether the message is related to any other messages. The footer or 'signature' consists of several lines of optional information composed by the sender, and automatically appended to all that sender's messages.
In Sally's case, her signature contains her home and university postal addresses, and also the electronic addresses she uses on several other networks. It also contains a brief literary quote which she is fond of sharing with other network users.
Characteristics of Electronic Network Communication
Having learned how to access a BBS, information system, or multi-node network, and having mastered the commands necessary to move around its various areas, the new user will no doubt be surprised and confused by both the volume and the content of the stream of messages scrolling past on his computer screen.[2] A small, relatively unknown BBS might only carry a few desultory messages each week, but on many systems and networks it is not uncommon for from several hundred to several thousand new messages to be posted within any single twenty-four hour period.
It would be physically impossible to read all of these messages, and one of the first things a network newcomer must learn is how to navigate through the various hierarchical levels of the system, and select only the forums or groups in which he has a specific interest.
Information Overload
Having selected the forums or groups he wishes to read, the new user is presented with a stream of messages embedded in a matrix of referential information. The untrained eye will find it difficult to differentiate such information from the text of the message itself, and will tend to read everything presented on the screen. With time, however, the user will learn to ignore selectively such data as time of posting, presence or absence of replies, address of poster, routing of message, etc., and his eye will automatically skip to the message itself.
The quantity of referential data varies from network to work, and is proportional to the complexity of the message traffic.
Taking the user address as an example, that of a single-node BBS or information system user usually consists of a name, nickname, or code number. This suffices to identify that user and provides him with a unique address. The length of a multi-node network address, on the other hand, graphically illustrates the complexity of the message routing within such a system.
A multi-node network address may be linear or hierarchical. A linear address consists of a list of computer sites that a message needs to pass through to reach its destination. To turn once again to the postal service analogy, such a linear address is equivalent to writing on an envelope all the post offices through which a letter must go, and moreover writing them in their correct order. Such a linear address is often called a 'bang' address, referring to the exclamation marks or 'bangs' which separate each segment.
A hierarchical address, on the other hand, lists a structured hierarchy of computer sites in exactly the same way that a postal address lists country, province, city, street, house number, and name. Such an address is usually referred to as a 'domain' address, and can only be used on networks which make use of online databases containing information about node location.
The length and complexity of message headers can often get out of hand, overwhelming the text of the message itself. It is not uncommon to see a one- or two-line message embedded in up to ten lines of header and signature information. Some systems, indeed, have facilities for controlling the amount of such referential data displayed on the screen. This applies to the headers placed at the beginning of each message, but does not apply to the personal signatures which many posters append to the end of their message.
Threads
Once he has learned to cope with the flood of referential information, and learned to separate the text of the message from the data in which it is embedded, it may be thought that the user can now sit back and enjoy reading the messages in his forum or group of choice. Such is not the case.
Most new users find it extremely difficult to understand the content of the messages they read.
One reason is obvious: anyone joining an ongoing conversation or discussion needs time to pick up the thread of the topic.
Another less obvious reason is the complex interleaving of topics that takes place. A specific message might stimulate several replies, each dealing with the original message from a different perspective, and each raising different related issues. Each of these replies might stimulate replies of its own, and the topic will fragment into several separate but related subtopics or 'threads'.
Temporal constraints such as time of posting and speed of transmission within the system may also generate irregularity in the order and frequency of messages belonging to such subtopics.
The flow of messages within a multi-node system is neither continuous nor regular. Messages arriving at a particular node are stored until the computer is ready to pass them on to other computers in the network.
A large node such as a major university or user group may receive and send thousands of messages each day, processing them in batches of several hundred at a time, and at intervals of an hour or less.
A minor node may only be able to devote an hour or two a day to processing and transmission, and any messages routed through such a node will be held up for several hours before being sent along to the next node.
In a single-node system an interval of hours or days may elapse between the posting of a message and the posting of a reply. Whatever the length of the interval, an orderly cycle of post–read–reply is maintained. A specific topic might generate a number of interleaved subtopics, making it more difficult to follow the discussion, but the sequence of messages relating to any one subtopic will maintain temporal and thematic integrity.
In a multi-node system, however, it is not uncommon for a user reading a public message forum to receive the reply to a question before the question itself. In this case the original question reaches the replier by a very short or efficient route, and the route from the replier to the eventual reader is also shorter (or more efficient) than that from the questioner to the reader.
If we try to represent schematically this phenomenon of fragmentation and interleaving, an orderly discussion of a single topic might take the following form:
Ex. 1
A1 A2 A3 A4 A5 A7 A8 A6 A9 A10
It will be noted that message A6 has been displaced, no doubt following a slower route through the system. Once readers have become aware of this phenomenon of displacement, it is usually not a major obstacle to comprehension.
The following pattern is more representative of the kind of interleaving that takes place on most networks.
Ex. 2
A1 A2 A3 B1 A4 B2 B3 C1 A5 A6 B4 B5 C2 B7 A7 A8 B6
Topic A has generated two subtopics, B and C. All three topics continue to be discussed, but in what may seem to be a random and irregular manner.
Were this an oral discussion, various self-regulatory forces would operate, and the discussion would refocus upon one or other of the topics raised. In an electronic network discussion, however, users are physically and temporally isolated from one another, and it is not uncommon for an interleaved set of topics to continue for some time.
Topic fragmentation and the related phenomenon of topic drift, in which replies tend to focus upon one of the subtopics rather than the original topic itself, may eventually result in confusion and loss of direction, and at this point the moderators of most network forums will step in and either close topics or redirect messages into new ones.
Many multi-node networks and some of the larger single-node systems provide 'threading' functions which automatically mark messages relating to a specific topic. A reader can use this function to skip unrelated messages and jump directly to the reply to a message he is reading. The system will remember where the reader was when the jump was made, and will return the reader to that point when the end of the thread is reached.
Quotations
The extensive use of quotations in messages is another characteristic of network messages, and represents a conscious attempt to counteract the effects of topic fragmentation and drift.
Someone joining the discussion represented in Example 2, and reading from message B3, would have difficulty deducing what was being talked about, and how the discussion had started.
This applies not only to new members. Many network nodes do not have the capacity to store more than a limited number of messages at any one time, and older messages are deleted as new ones are received. For example, a small node might only have the capacity to store the fifty most recent messages in any one topic. In the case of a relatively quiet forum, fifty messages might represent one week's traffic, but in a more active forum the daily traffic might well equal or exceed this number. Consequently, anyone returning to a forum after an absence of several days might find that many messages had been deleted, making it difficult to pick up the thread of the discussion.
For this reason quoting is encouraged, and many networks have automated 'include' functions to make it as simple as possible. Some networks, for example, supply prompts after each message, asking the reader whether he wishes to reply. If the reader responds in the affirmative, the system will ask him if he wishes to quote. If the answer is again yes, the system will automatically place (or 'paste') the entire original message into the reply, prefacing it with the name and address of the writer, and setting it off with indentation marks.
The writer of the reply should now use the editing function of the system to delete irrelevant lines of the quotation, but unfortunately many users do not. The quotation of a message in toto may be of benefit to a new member of a forum, but it can be irritating for regular members who well remember reading the original posting.
The quotation of a message which itself contains a quotation can lead to the phenomenon of nesting, with quotations-within-quotations, each level denoted by increased indentation.
Abbreviations
Another characteristic of electronic networks precluding the immediate and complete comprehension of messages is the widespread use of unfamiliar abbreviations and symbols.
Few of the commonly-used abbreviations are self-evident, as the following selection may illustrate:
ASAP = As Soon As Possible IMHO = In My Humble Opinion BTW = By The Way re = about FYI = For Your Information ROTF = Rolling On The Floor (Laughter) HAHAHA = (Laughter) UR = you are
It should be noted that whilst some of these abbreviations are employed to facilitate the rapid input of frequently-used expressions, others are used to inject a mood of levity or humour into the discussion, or to provide information about the attitude or emotion of the writer.
The use of symbols likewise serves the function of representing common non-verbal cues. The first five of the following examples should be viewed sideways.
:) = smile (smiley) :( = frown :-) = smiley variant :O = amazement/surprise ;) = wink <g> = grin
It is of great significance that many users of electronic networks should feel the need to supplement their messages with such crude substitutes for non-verbal cues. We shall return to this important point at a later stage of our discussion.
Quality of Writing
Another characteristic of electronic networks is the literary standard of the messages. Whereas individual messages may exhibit a high degree of literary sophistication, and the quality of messages in specific groups and forums may be very high, it is nevertheless true that the average standard of network traffic is rather low. It is rare to encounter a message which does not contain errors of grammar, orthography, or usage.
It would be precipitate, however, to assume that this reflects the educational achievement of the writers. It should be remembered that the global scale of such networks, and the ease with which they can be accessed, has resulted in a cosmopolitan user population. Although English is the language of preference, it may not necessarily be the first language of many of the users.
This is not to say that all such messages are the result of linguistic inexperience. Many messages posted by users for whom English is the first or indeed only language also exhibit this characteristic. Considerations of space permit the reproduction of only three illustrative examples, the first of which is taken from a discussion concerning the attitude of mainstream Christian churches towards Jehovah's Witnesses.
An additional thought,you almost sound like you think that people in the organization do not want to be there.Example, if someone in a opera or ballet disagreed with something,even a little something, but orders from the bigwigs who run the show disagree.The person with the problem ,if it means enough to them will just leave if everyone else agrees that the bigwigs are right.The only parrellel(?, can you believe that spelling) I am trying to draw is that if some doesn't agree,then why did they become a JW.One of the reasons for being baptized is so there are no emotional decisions,but heart ones based on knowledge. If they came up with questions afterwards,then they are helped to research the problem or come to a solution.If the person really didisagrees,why would they want to stay anyway,if it was important to them.And that is why some drift away.Never heard from again.Others take a more noticable or radical approach and if they are trying to cause problems(Tit. 3:10,11).Read topic 5 for more info on expelling. HeyBales [3]
The second example is taken from a forum discussion of Scientology, and was posted by a lady who descibed herself as 'a college graduate with Summa; and one step away from my own office.'[4]
When I look at those posts, without a solutation, it's like, come to attention, huh. Anyway, I think you understand my point. I don't see how Scn counselors cou counsel, in their own beliefe system; if they WERE NOT a church, religion. They'd have to follow other state requirements. I don't know if that is right or wrong, but I don't understand how a person could use THE TECH and not be within the confines of the protection of THE CHURCH. Just a thought. -------------- Ok Eric,
My experience is only with the volunteer side of the church; I don't know the percentages. Now the volunteer side, is full time; so it's not volunteer in what I volunteer for, now with local libraries and such. Some people held down two jobs, one volunteer and the other to pay the rent. I don't know what the pay structure is now, it was well, not minimum wage... it was based on what came in for the week.
Most of the church today, are staffed with these volunteers, but don't have a statistic, it was not something I ever thought about. Interesting... ---------[5]
The last example comes from a network forum dedicated to a discussion of Japanese language and culture.
Manabu-San, Friends, who have been here to help, I have a poem (haku?). To those who have heard the paper tears of my mind "dark cold moutain, rather then counting the rows of Corn in the sunshine of Dreams" "mirrors, show you where you sit" only Winston, can put the coller on Churchill's "Black Dog" My dog, is Healed! Chessplayer YOUR MOVE! ----------- I THINK THAT IS RELEVANT TO WHAT'S "FAIR" I WILL TALK MORE SOON , BUT I HAVE TO GO OUT AND ENJOY LIFE WITH MY WIFE.GARY BROWN, AIRCRAFT MECHANIC, SAN FRANSCICO Manabu-san you have my permision to use or remove what ever you see fit in this massage. to those who have been here to help it would be good to play chess with you I like your- game! I am honored to be a member of this club. gary [6]
It may be thought that quotation out of context has made the above message illegible. Such is not the case. The user in question posted several longer and equally unintelligible messages in several different categories and topics, and was eventually demoted to read-only status.
Flames
The final characteristic we shall examine is the tendency of discussions to develop into acerbic and vindictive personal argument. An ill-chosen word or phrase, or a misinterpreted statement or comment can spark off a hasty and emotionally-charged reply, which in turn calls forth a similar response. The suddenness with which such a dispute can begin and the rapidity with which it can spread and engulf other users has lead to this phenomenon being called a 'flame'. Although most flames will eventually die out as misunderstanding is removed, some may require the intervention of a forum moderator to prevent them escalating further.
By far the most common cause of flames is spelling. Comments drawing attention to spelling mistakes in previous messages are prone to produce angry reactions from the writers of those messages. For this reason, many networks warn users to resist the temptation to criticize spelling mistakes or, for that matter, any lapses of grammar or usage.
Other common causes of flames are personal remarks or suggestions. Innocent and well-meaning comments are often interpreted as criticism, and evince emotional replies. Once begun, a flame can continue for days or weeks, and may involve a hundred or more messages.
Perhaps a brief summary of a selected example might help to show how a typical flame is generated, how it develops, and how it is eventually extinguished.
A new member of a forum dedicated to discussion of topics related to the English language posted a question about the meaning of an unknown neologism she had encountered in her reading. We shall refer to this lady as Lynn.
Is "infomatic" a real word? I saw it a few days ago and it's been bothering me ever since? - Thanks! [7]
The response was prompt. Within hours, several of the regular forum members (Group A) posted replies describing how they had consulted various dictionaries and had failed to find a definition of the neologism in question. Lynn retorted that the habit of referring to a dictionary for the clarification of unknown words was one she had acquired in elementary school, and she had, of course, consulted several dictionaries before posting the original message.
Group A members now responded that it was no intention of theirs to suggest she did not know how to use a dictionary. Lynn did not reply to these messages, but several other members of the forum (Group B) took her side in the dispute, pointing out that it was difficult to interpret Group A's messages other than as an implied criticism that Lynn had not taken the trouble to consult a dictionary before posting her first message. Group A insisted that they were only trying to be helpful, that no criticism was intended, and that their first replies were motivated by a desire to report the results of their own research. Group B maintained that Group A should have thought twice before posting their messages. The dispute was kept in a very low key by the liberal use of smiley marks, signalling that critical remarks were not to be taken too seriously. At least one member suggested that the dispute might have been avoided in the first place had Lynn likewise softened her second message with such marks.
At this point Lynn rejoined the discussion with the following posting:
Lynn again. Sorry if I seemed rude. I honestly thank everyone for their effort. I am a new user (trial, actually) to this, so I couldn't understand the happy faces. :-) They're cute. Thanks and sorry for the troubles. [8]
The group moderator's response to this apology was extremely illuminating:
Thanks for the apology, Lynn. Smiley-faces are more or less a necessity on BBS systems; we don't have the para-linguistic cues (facial expressions, gestures, etc.) to provide extra meaning, so we sometimes misinterpret the tone of messages. I certainly hope that this situation hasn't put you off of modeming and hope that you'll stay with us here on Mind Link! :-) [9]
It should be noted in passing that Lynn never did receive a satisfactory answer to her original question about the neologism.
Discussion
Before entering into a discussion of the themes we have introduced so far, it may be helpful to summarize some of the characteristics of electronic network communication we have mentioned thus far.
Although network communication bears a superficial resemblance to traditional forms such as the letter, there are a number of significant differences. Both forms begin and end with a written message, but the similarity ends here.
The widespread use of personal computers and the growth of computer networks has made possible the speedy and efficient transmission of written messages. A network user can compose a message upon his computer at home, and be certain that several thousand or several hundred thousand other computer users throughout the world will be able to read his message within minutes or hours of its posting.
Electronic networks have given the individual computer user the power to communicate his thoughts and feelings to a vast audience; they have democratized communication itself, causing much consternation among governmental agencies responsible for internal security; they have also imposed certain distinctive constraints upon the process of communication, thereby affecting both the form and the content of the messages the medium transmits.
On the one hand, the electronic network medium has made the writing, transmission, reception, and reading of written messages simple and convenient. On the other hand, it has introduced complexity and confusion into the process. The powerful word processing tools that computers place in the hands of the writer should have resulted in more finely crafted communications, communications better able to express the thoughts and emotions of the writer. The quality of the messages circulating on most networks suggests that the opposite is true.
Why should this be? One hint is to be found in the frequent use on electronic networks of the abbreviations and symbols mentioned earlier. For some reason, many users of electronic networks feel the lack of non-verbal cues, and attempt to supplement their messages with crude signs representing, among other things, smiles, winks, frowns, laughter, and surprise.
In traditional written communications, the linguistic and semantic complexity of the written language serves to compensate for the absence of non-verbal clues to the attitude of the writer. Careful choice of vocabulary and phrasing ensure that irony, for example, is seen for what it is, and not mistaken for a direct expression of the writer's feelings.
Another hint is provided by the prevalence of spelling and grammatical mistakes in network messages. Some of these are the result of ignorance or incompetence, but many are clearly the result of carelessness. Spelling mistakes such as transposed letters point to hasty typing, and the occurrence of redundant words and incomplete phrases shows careless use of cut-and-paste editing functions.
It bears repetition that this is precisely the opposite of what one might expect. Computer word processing facilitates the unlimited manipulation of text and format, the electronic correction of spelling, and even the electronic checking of grammar and style. No text composed upon a computer screen need be printed out or transmitted until the writer is completely satisfied with the result.
If almost every item of word processing software contains spelling check functions, and the use of such functions entails only a few key-strokes and a matter of only a few extra seconds, why then do so many network users litter their messages with <sp?> signs, signalling that they are not sure of the correct spelling of a word. If they are not sure of the spelling, why do they not refer to a dictionary, or run an electronic spelling check?
One answer to all these questions is haste. The writers did not have time to reread and correct their messages before posting, nor did they have time to run spelling checks for orthographical or typographical errors. Messages composed in haste tend to fall back to the linguistic and semantic complexity of speech, and represent transcriptions of internalized, unvocalized conversational components. The writers are, to use a colloquialism, writing off the top of their heads, committing to text the stream of words forming in their minds. Being representations of unspoken conversation, such messages lack the sophistication of carefully written communications, and are less able to give expression to subtle nuances of thought and emotion. Hence the perceived need for symbols representing the non-verbal cues of spoken interactions.
Having identified haste as one of the factors contributing to some of the characteristics of electronic network communications, we must ask ourselves what the cause of this haste might be. What is it that induces network users to post messages without checking them for elementary mistakes?
Some networks charge users according to the time spent online, and it may be that users feel the pressure to write their messages as quickly as possible. This may be true for messages written online, but it is a simple enough matter to log off the network, compose a message at leisure, and then log on again to upload the message. Not only does this technique allow the writer to compose his message in his own time, and thus produce a more coherent and articulate communication, it also significantly reduces online charges. If some users persist in writing messages online, it is once again because they feel under some kind of pressure to post their messages as soon as possible.
Where does this pressure come from? It is our suggestion that this pressure is generated by the speed and volume of messages flowing within the networks themselves, and is therefore a function of the medium itself.
One of the advantages of electronic network communication is the freedom the user enjoys to access the medium at a time of his own choosing. Some users may wish to log on to a network once a day, others at intervals of a week or more. A reply to a message can be posted immediately, or it can be posted hours or days later.
The message traffic on an electronic network does, however, have a characteristic rhythm and pace of its own. The average interval between consecutive messages within a specific topic will, of course, vary according to the forum or network. Popularity of topic, number of forum members, geographical distribution of network, physical organization of system — all these factors can affect the flow of messages. Be that as it may, anyone posting a message within a specific topic can be reasonably sure that someone else will post the next message in that topic within a matter of minutes.
This awareness generates pressure upon forum members to answer as quickly as possible. If a topic is concerned with an exchange of information, a delay might make the information redundant. If the topic is concerned with an exchange of ideas, a delay might make the opinion irrelevant.
If, for example, a forum member posts a message requesting a specific item of information, another member possessing that information, but delaying his reply, might find that other members had already posted the required information ahead of him, making his message redundant.
Similarly, anyone procrastinating over the posting of a message containing a contribution to a discussion or debate might find that the topic had moved on to other considerations, and that his opinion was now irrelevant.
In this respect, the pattern of interaction within a network forum is similar to that within a discussion or conversation. A participant in a spoken discussion who ignores the natural rhythm and pace of remarks and utterances, and speaks out of step, will render no service to the group, and will earn the group's disapproval.
In our earlier remarks about the physical process of network communication, we noted that perhaps the most efficient way of reading messages is to download them in bulk, save them onto a floppy disk or other storage medium, and then read them at leisure. Likewise, the most efficient method of posting messages is to compose them offline, using the full capabilities of a dedicated word processing program, and then upload them to the network as complete documents.
Any user adopting these techniques can maintain files of earlier message traffic, can refer to those messages at will, can quote from them, and can incorporate them into his own postings, adding to the integrity of topic development.
Few users, however, choose to do so. Time is not a consideration in this decision. Many telecommunication software applications can be set up to store messages automatically in preselected files. What is a consideration in this decision not to archive messages is the volume of message traffic itself.
It is not uncommon for a user to access several forums on a number of networks, and were he to preserve all of the messages flowing into his computer, he would soon find himself running out of both storage space and the time needed to organize and maintain the archives. Different forums would require different files, and as new messages came in old files would have to be opened, added to, and saved again. Most new network users attempt to maintain such archives. Most give up after only a few weeks, having lost themselves within a veritable deluge of messages.
One other problem remains to be addressed in our discussion. We have suggested that the speed and volume of message traffic on networks is one of the factors contributing to some of the characteristic features of network communication. We have not yet examined the possible causes of the flames which frequently break out on network forums.
In one respect, flames may likewise be the result of pressure upon the user to respond quickly. Messages written and posted in haste may be less capable of articulating the writer's thoughts and emotions, and more apt to generate misunderstanding. A closer study of typical flame patterns suggests, however, that other factors may also be at work.
A flame can originate with a statement or a response. An aggressive comment on a sensitive subject such as religion or politics may produce a flood of angry messages. On the other hand, a relatively innocuous comment may be misinterpreted by a reader, and may stimulate an irate response.
It should be noted that some flames are started deliberately by irresponsible network users who take a perverse pleasure in the emotional reactions their messages produce. Some networks tolerate such users, others take action against them, closing their accounts, banning them from certain forums, or limiting them to read-only status.
Aware of the destructive effect of an uncontrolled flame, most responsible users take care to avoid sensitive issues, or try to lessen the impact of problematic statements by the use of self-deprecating humour. As we saw in the example quoted earlier, smiley symbols can be used to show that the writer does not take his message too seriously, and to express the hope that neither will his readers. Another effective technique is pre-emptive action. Many users preface statements likely to cause angry responses with humorous asides about donning asbestos suits or reaching for fire extinguishers.
In any spoken discourse, the discussion may sometimes get heated and tempers frayed. The explosive intensity of network flames, and the rapid reduction of debate into personal invective, is of an entirely different order.
The most obvious difference between spoken discussions and their network counterparts is the size of the audience. Whereas in most discussions the participants form their own audience, the exchange of messages on a network might have an audience of several thousand. The participants in a network debate cannot help but be aware of this enormous audience of readers.
It is for this reason, we suggest, that reactions on networks can be so extreme. What is at stake is not the esteem of several colleagues in a small room, but that of thousands of strangers on a nationwide or global network. A perceived slight or insult within a small-group situation is of relatively small importance, and group dynamics can quickly identify such a perception and take steps to correct it. If a physically isolated user on a network feels he has been ridiculed or insulted in front of several thousand people, the vehemence of his reaction will be correspondingly greater.
We have concentrated thus far upon some of the negative characteristics of network communication, and have suggested that they might be the result of various constraints and pressures imposed by the medium itself.
It would be disingenuous, however, not to acknowledge other contributory factors, not the least being education. The mediocre literary standard of the majority of messages on networks may have part of its origin in the falling standards of literacy reported by many so-called 'developed' countries.
On the basis of individual network messages it is almost impossible to ascertain whether the writer could have produced a more literate and articulate piece had he been given sufficient time. Many spelling mistakes, for instance, could be the result of either ignorance or typography. Given the present levels of literacy in English-speaking countries, however, it is not difficult to imagine that better English language education at school would probably result in more articulate communication. Users better trained in language skills would be able to produce more fluent messages, and be less sensitive to the effects of pressure.
Topic drift and topic fragmentation could likewise have part of their origin in lack of training in rhetoric and debate. Users equipped with basic rhetorical skills, it might be argued, would be better able to compose articulate messages relevant to the topic under consideration, and would express themselves clearly and unambiguously, thereby reducing the possibility of misunderstanding and network flames. Put another way, educated and articulate users would be able to overcome the physical limitations of network communication in much the same way that a gifted writer overcomes the physical limitations of a battered old typewriter.
The question remaining to be asked is how much of the mediocrity of network communication can be attributed to the effects of the medium itself, and how much to the lack of training in language and communication skills.
Nothing less than a massive study comparing the quality of thousands of network messages with national standards of literacy could provide a satisfactory answer to this question, and it is doubtful whether such a study will ever be conducted.
Changing attitudes towards education and the relativization of standards of literacy have made it increasingly difficult to pass judgment on language use, and even if all other considerations were to be subordinated to that of communicative efficiency, it would be difficult, if not impossible, to determine how effectively individual messages had communicated the intentions of their writers.
It may also be that other electronic media have had an effect upon network communication. Television, in particular, has dramatically changed the way information is presented, reducing complex subjects into short episodic presentations of images supplemented by commentary. Some topics may lend themselves to such treatment, but others most certainly do not. In the case of the latter, the medium of television only succeeds in trivialization, in giving the illusion of having informed where it has only stimulated.
Daily exposure to the medium of television may have subconsciously influenced the way in which many network users structure and present information, engendering a reluctance to enter into complex dialogue, and a tendency to rely on oversimplification reinforced by emotional pointers.
The use of computers itself may have some connection with the standard of literacy and discourse on networks. Recent controversial studies have suggested that the speed and ease with which ideas can be converted into high-quality printed output rivalling that of traditional printing methods has encouraged writers who rely on computer word processing to skip important stages of the creative process, devoting less time to organization of ideas and critical rewriting.[10]
These studies have concentrated on comparisons between different user interfaces, but to be of any significance, a much wider comparison would have to be made of the literary output of writers using word processors, those using the traditional medium of pen and paper, and those using transitional media such as typewriting.
Conclusion
Whether the characteristics of network messages examined in this report are the result of a combination of inadequate education, media influence, and computer use, or whether they are, as we have suggested, the product of the medium itself, only time will tell. The problems of information overload and individual choice are being addressed, and electronic networks may one day approach the transparency of carefully structured media such as the Compact Disc.
Of the millions of people who enjoy the quality and convenience of CD recordings, few indeed are aware of the fact that a significant proportion of the data on each disc is not music or sound, but supplementary technical information. This information is completely invisible to the user, but it is this information which enables the user to skip tracks at will, to select programmes of songs, or to repeat sections of the recording.
The dilemma of electronic information exchange is that the more information a medium presents to the user, the more necessary it is to control the flow of information and to exercise choice. This can be accomplished, but it requires the use of even more information, and this additional information must be made invisible to the user if its very purpose is not to be vitiated.
If network communication becomes significantly more transparent and user-friendly, we may assume that some of the problems we have examined will be resolved, at least in part. Messages should become easier to find, easier to read, easier to manipulate, and easier to write. This may lead to an improvement in quality of writing and discourse.
On the other hand, it may be that technical advances at present under development will result in a hybrid medium which combines word, sound, and image. It is not difficult to foresee oral input of messages, bypassing the use of traditional keyboards. From there it is only a relatively small step to the development of an audio-visual medium in which messages would consist of sound and image. The exchange of written messages via electronic networks might prove to be only an evolutionary stage in the development of another medium.
It is difficult to see, however, how technical improvements in the medium itself will ever resolve the problems of communicative skill and audience sensitivity. Perhaps the only way to address all the problems we have examined is to supplement technical improvements with better education in language and communication.
NOTES
1 In alphabetical order: BC Macintosh, BMUG, Generic, GEnie, MacLink, Mind Link!, Questor, Sunshine, Usenet.
2 For the sake of clarity and legibility, in the general discussion that follows the author has adhered to the literary convention of using the generic pronominal forms 'he', 'his', and 'him'. This is in no way to ignore the participation and contribution on electronic networks of a significant number of female users.
3 GEnie, Religion & Ethics RoundTable Bulletin Board, Category 15, Topic 12, Message 15.
4 GEnie, Religion & Ethics RoundTable Bulletin Board, Category 15, Topic 23, Message 255.
5 GEnie, Religion & Ethics RoundTable Bulletin Board, Category 15, Topic 23, Message 245.
6 GEnie, Japan RoundTable Bulletin Board, Category 1, Topic 2, Message 27.
7 Mind Link! Message #733605.
8 Mind Link! Message #742183.
9 Mind Link! Message #742680.
10 Vid. Steven Levy, "The Iconoclast: Does the Mac Make You Stupid?," Macworld (November 1990) for an interesting introduction to the controversy.
Source: Otsuma Women's University Annual Report: Humanities and Social Sciences, Vol. XXIII, 1991